


Courses Gaining Global Popularity Among Students

Most Popular Courses Students Are Choosing Worldwide
Trending Online Courses in 2025: Top Benefits and How to Choose the Right One
Online courses in 2025 offer a flexible and effective way for students and professionals to acquire new skills and advance their careers.
Top Trending Courses in 2025 for Students and Professionals

Graduates can work in hotels, resorts, travel agencies, and event planning companies.
Upskilling in 2025: Key Trends and Courses Professionals Should Consider

As we move into 2025, professionals must take a proactive approach to upskilling, focusing not only on technical expertise but also on soft skills, leadership,
Top Courses in 2025: Most In-Demand Study Abroad Programs for Indian Students

the most in-demand courses for Indian students in 2025 reflect both global industry needs and individual aspirations for career growth and stability. Choosing
Top 24 Trending Online Courses in 2025: Boost Your Career with In-Demand Skills

These courses not only provide technical expertise but also offer opportunities for career growth, with many programs featuring industry collaborations and plac
Ethical Dilemmas in Offensive Cybersecurity Operations
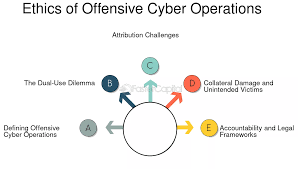
Ethical Dilemmas in Offensive Cybersecurity Operations
Cybersecurity for Brain-Computer Interfaces (BCIs)
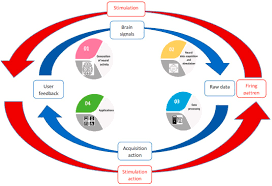
Cybersecurity for Brain-Computer Interfaces (BCIs)
Cyber Insurance and Its Impact on Corporate Security Policies
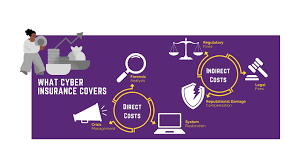
Cyber Insurance and Its Impact on Corporate Security Policies
The Dark Web Economy of Exploit Kits and Malware-as-a-Service (MaaS)

The Dark Web Economy of Exploit Kits and Malware-as-a-Service (MaaS)
Supply Chain Cybersecurity in Open Source Software Ecosystems
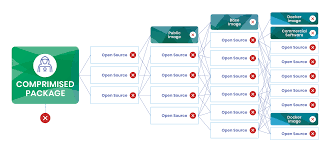
Supply Chain Cybersecurity in Open Source Software Ecosystems
Ethical Hacking with LLMs and Autonomous Pentesting Agents
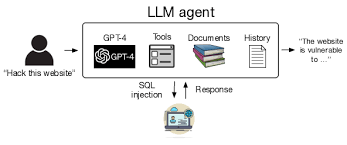
Ethical Hacking with LLMs and Autonomous Pentesting Agents
Insider Threat Detection Using Behavioral Biometrics
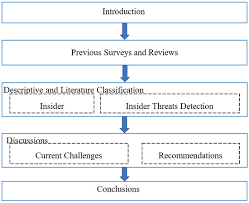
Insider Threat Detection Using Behavioral Biometrics: A Smart Solution to Protect Your Business
IoT Device Regulation and Global Security Standards
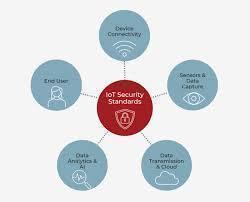
IoT Device Regulation and Global Security Standards
Hacktivism and Cyber Warfare in Geopolitical Conflicts
The Role of Hacktivism and Cyber Warfare in Global Conflicts
Cybersecurity Risks of Augmented Reality (AR) and Virtual Reality (VR)

"Hacked Realities: Cybersecurity Challenges in AR and VR"
Deepfake Detection and Response in Cybersecurity

Protect Yourself from Deepfakes with Smart Cybersecurity Steps
The Human Firewall: Training Yourself to Spot Cyber Threats

How to Be the Human Firewall and Stay Safe Online
Real-World Cybersecurity Case Studies Students Can Learn From

Real-World Cybersecurity Case Studies Students Can Learn From
Cyber Law and Digital Rights: What Every Student Should Know

Cyber Law and Digital Rights: What Every Student Should Know
Biometric Authentication: Are Fingerprints and Face ID Truly Secure?
Biometric Authentication: Are Fingerprints and Face ID Truly Secure?
Cybersecurity for Online Exams and Virtual Classrooms
Cybersecurity for Online Exams and Virtual Classrooms
Mobile Security: Are Your Apps Spying on You?

How Everyday Apps May Be Collecting Your Personal Data Without You Knowing
Ethical Hacking: Why White Hat Hackers Are in Demand

Ethical Hacking: Why White Hat Hackers Are in Demand
IoT Security: Protecting Smart Devices at Home and School
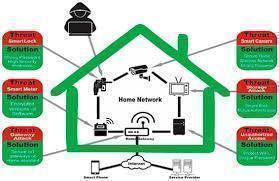
IoT Security: Protecting Smart Devices at Home and School
Understanding Ransomware: Anatomy of an Attack

Why Ransomware Is One of Today’s Biggest Online Threats
Cybersecurity Careers: Roles, Skills & Certifications in 2025
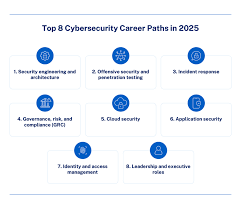
Cybersecurity Careers: Roles, Skills & Certifications in 2025
Zero Trust Architecture: The Future of Network Security
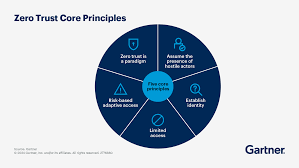
Zero Trust Architecture: The Future of Network Security
Social Engineering Attacks: How Hackers Manipulate Human Behavior
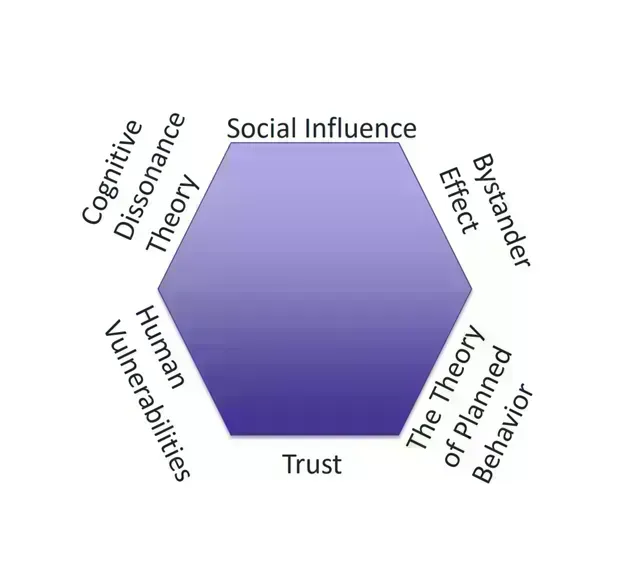
Social Engineering Attacks: How Hackers Manipulate Human Behavior
The Dark Web Explained: What Students Need to Know
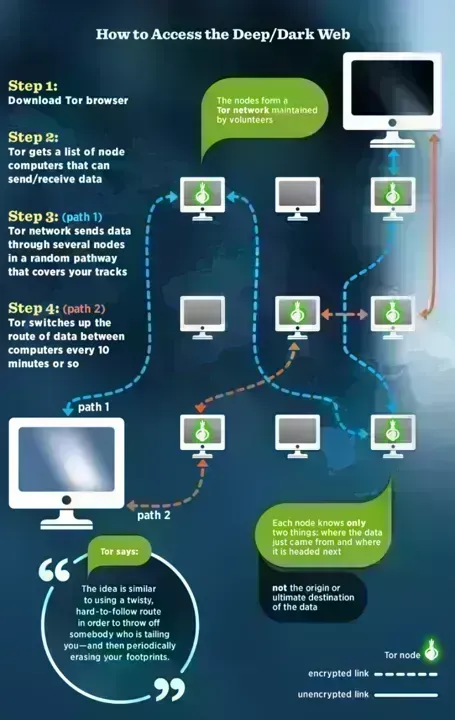
The Dark Web Explained: What Students Need to Know
Cyber Hygiene: Best Practices for Students and Educators

Cyber Hygiene: Best Practices for Students and Educators
The Rise of AI in Cybersecurity: Opportunities & Threats
The Rise of AI in Cybersecurity: Opportunities & Threats
The Importance of Cybersecurity Education in Schools

The Importance of Cybersecurity Education in Schools
Social Engineering Attacks: Why Awareness Is Your Best Defense
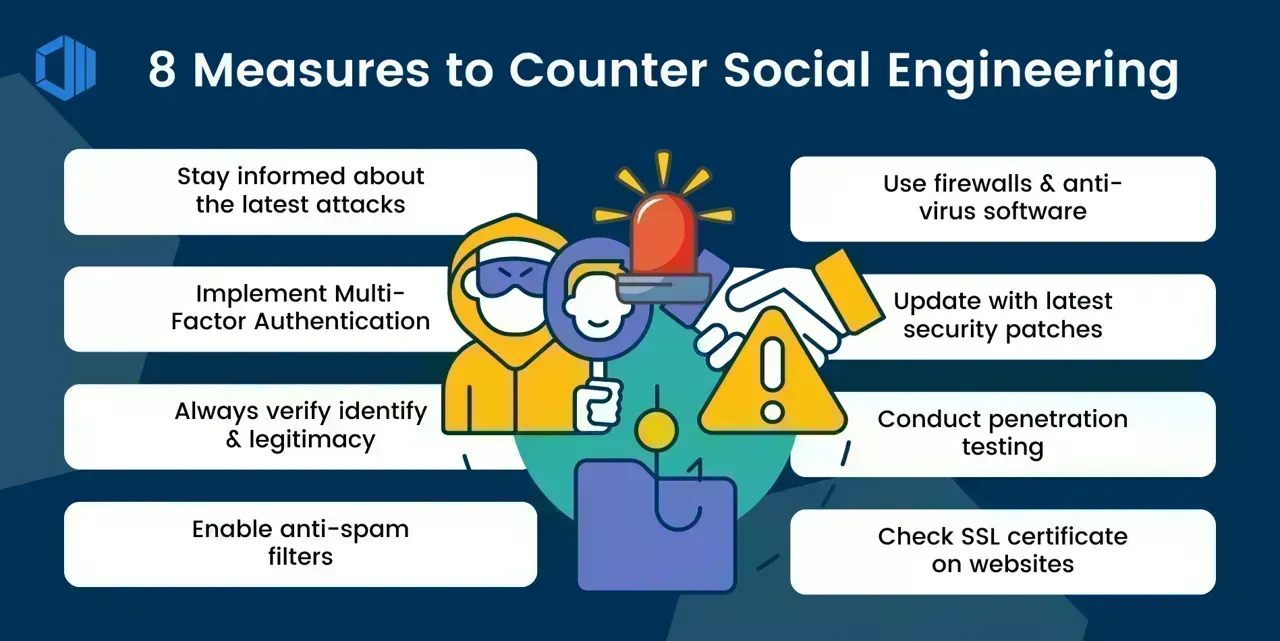
Think Before You Click: The Truth About Social Engineering Attacks
Data Privacy in Education: Are Your School Apps Safe?
Data Privacy in Education: Are Your School Apps Safe?
Careers in Cybersecurity: What Students Need to Know

Careers in Cybersecurity: What Students Need to Know
Cyber Hygiene: Digital Safety Habits Every Student Should Follow

Cyber Hygiene: How Students Can Stay Safe Online
Top 5 Cyber Threats Facing Schools and Colleges Today

Explore the Top 5 Cyber Threats Targeting Schools and Colleges Today
Cybersecurity for Students: How to Stay Safe Online

Stay Safe Online: Protect Yourself from Hackers, Theft, and Scams
The Impact of Cybersecurity on Educational Institutions
Protecting Student Data The Role of Cybersecurity in Schools

Sensitive data of vulnerable children leaked online.
UnitedHealth Seeks Hack Loans Back

UnitedHealth wants repayments for cyberattack loans to providers.

O’Brien holds clear lead over Bowen in recent showdown.

CTX Python library found malicious, removed from PyPI repo.
 Fake posts hit Czech PM Fiala's X
Fake posts hit Czech PM Fiala's X
Fake posts disrupt Czech PM Fiala's X account security
 Yemen strike plans leaked on Signal
Yemen strike plans leaked on Signal
Yemen attack plans were exposed on Signal, raising big risks.
 Child Data Leak Exposes Risk
Child Data Leak Exposes Risk
Sensitive data of vulnerable children leaked online.
 UnitedHealth Seeks Hack Loans Back
UnitedHealth Seeks Hack Loans Back
UnitedHealth wants repayments for cyberattack loans to providers.
 O’Brien Edges Ahead of Bowen
O’Brien Edges Ahead of Bowen
O’Brien holds clear lead over Bowen in recent showdown.
© MyEduGoal. All Rights Reserved. Design by markaziasolutions.com