


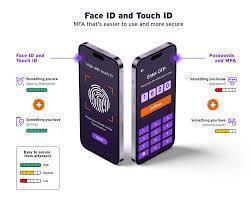
Biometric authentication, including methods like fingerprint scanning and face recognition (Face ID), has become increasingly popular as a way to secure devices and services. These technologies promise convenience and high levels of security, as they rely on unique physical or behavioral characteristics to verify identity. However, the question arises: Are fingerprints and Face ID truly secure?
In this article, we will explore the security of biometric authentication systems, their vulnerabilities, and how they compare to other methods of authentication.
Biometric systems authenticate a person based on physical or behavioral traits, which are believed to be unique to each individual. The most common types of biometric authentication include:
Fingerprint Recognition: Scans the unique patterns of ridges and valleys on an individual’s fingertip.
Facial Recognition (Face ID): Uses facial features such as the distance between the eyes, nose, and mouth to create a facial map.
Iris Scanning: Analyzes the unique patterns in the colored part of the eye (the iris).
Voice Recognition: Uses the unique characteristics of a person’s voice, such as pitch, tone, and cadence.
Behavioral Biometrics: Analyzes patterns of behavior, such as how a person types or walks.
Both fingerprints and Face ID are the most widely used methods, particularly in smartphones and laptops.
Biometric systems offer several advantages over traditional forms of authentication like passwords or PINs:
Convenience: Biometric authentication is fast and easy—fingerprint scanning and Face ID are often more convenient than entering a password.
Hard to Forget or Lose: Unlike passwords, you cannot forget your fingerprint or face. This makes biometric methods ideal for daily use.
Higher Security Potential: Biometric features are unique to individuals, making it difficult for attackers to impersonate someone.
Despite the advantages, both fingerprints and Face ID are not impervious to attacks. Below are some potential security risks associated with these methods:
Fingerprint Replication:
High-Resolution Photos or Molds: It’s possible for a hacker to replicate a fingerprint using a high-resolution photo of a fingerprint or by lifting a print left behind on surfaces. With enough detail, criminals can create a 3D mold of the fingerprint and bypass fingerprint authentication.
Fake Fingerprints: Sophisticated tools can be used to create fake fingerprints, though it requires high technical expertise.
Stolen Fingerprint Data:
When fingerprint data is stored on a device or cloud server, it is often stored in an encrypted form. However, if an attacker can gain access to this data, they can potentially steal fingerprints. Unlike passwords, biometric data like fingerprints cannot be changed if compromised. If a database containing fingerprint data is breached, it may be a permanent security issue.
Quality of the Sensor:
Not all fingerprint sensors are created equal. Some low-quality sensors may have higher rates of false positives (incorrectly identifying someone as authorized) or false negatives (denying access to an authorized user), which can undermine the security of the system.
3D Models and Photorealistic Masks:
In some cases, attackers have been able to spoof Face ID using high-quality photos or 3D-printed models of a person’s face. While Apple’s Face ID is designed to differentiate between a real face and a 2D photo, hackers can create sophisticated 3D models that could bypass certain systems. However, the technology is improving to detect more realistic 3D representations of a person.
Liveness Detection:
One of the major improvements in Face ID systems is liveness detection, which checks whether the face is a real, living person or a photograph or video. Still, there are instances where high-tech masks or deepfake technology can potentially fool liveness detection.
Although Apple claims that Face ID is secure enough to prevent spoofing through photos or videos, reports have surfaced where attackers have used high-definition photos or advanced 3D models to defeat Face ID.
Privacy Concerns:
Unlike passwords, facial features are public by nature. A hacker could potentially obtain a clear image of your face from social media or public videos. Though Face ID data is encrypted and stored locally on the device, it is not impervious to breaches if the data is ever stolen.
There are also concerns about facial recognition being used without consent, such as by law enforcement or corporations collecting biometric data in public spaces.
Passwords: Passwords can be stolen, guessed, or hacked through techniques like brute-force attacks or phishing. However, they can be changed, unlike biometric traits, making passwords more adaptable in case of a breach.
Two-Factor Authentication (2FA): 2FA adds an extra layer of security by requiring two forms of verification, typically something you know (password) and something you have (like a phone or authenticator app). It’s considered more secure than biometrics alone, as it reduces the risk of an attacker gaining access even if they have your biometric data.
Hardware Tokens: Physical tokens, like USB security keys, offer a higher level of security than biometrics. These devices are difficult to hack and cannot be replicated remotely. However, they are less convenient than biometric methods.
Despite the risks, biometric authentication does provide some advantages in certain contexts:
Convenience and Speed: Biometric methods provide faster and more seamless access than typing passwords, which is particularly useful in mobile devices and high-traffic environments.
Reduced Password Fatigue: People often reuse weak passwords or choose easy-to-remember ones, which are more prone to being cracked. Biometric authentication circumvents this issue by removing the need for remembering passwords.
User Experience: Biometric authentication often delivers a smoother and more intuitive user experience compared to traditional password-based logins.
If you want to make biometric authentication more secure, consider the following measures:
Combine with Multi-Factor Authentication (MFA): Adding a second factor (e.g., a PIN or password) alongside biometric authentication can significantly increase security, even if someone manages to spoof your fingerprint or face.
Ensure the Use of High-Quality Sensors: Devices with high-resolution sensors and liveness detection are harder to spoof and provide more accurate readings.
Local Storage of Biometric Data: For enhanced privacy, biometric data should be stored locally on the device, not in the cloud, to reduce the risk of mass data breaches.
Keep Software Updated: Regularly update the biometric authentication software to ensure that it has the latest security patches and improvements.
Biometric authentication, including fingerprints and Face ID, offers significant advantages in terms of convenience and potential security. However, they are not foolproof. Both systems have vulnerabilities, such as the potential for spoofing or data theft, which can compromise their effectiveness.
Are they secure? Biometric methods are more secure than traditional password-based systems, but they are not immune to attack. The key is to balance security with convenience, which is why multi-factor authentication (MFA) combining biometrics with another form of verification (such as a PIN or token) is often recommended for enhanced protection.
Biometric authentication is likely to remain an important component of digital security, but users and organizations should be aware of its limitations and take additional steps to secure their devices and personal data.
#trending #latest

University Internships That Help You Get a Job After Graduation... Read More.

Is It Smarter to Start at a Community College... Read More.
 Fake posts hit Czech PM Fiala's X
Fake posts hit Czech PM Fiala's X
Fake posts disrupt Czech PM Fiala's X account security
 Switzerland Tightens Export Rules
Switzerland Tightens Export Rules
Switzerland expands export controls on dual-use goods
 Google unveils Ironwood AI chip
Google unveils Ironwood AI chip
Google introduces Ironwood chip to accelerate AI tasks & apps
 TSMC Q1 revenue up 42%
TSMC Q1 revenue up 42%
TSMC sees 42% revenue surge in Q1, surpassing forecasts
 Amazon CEO Outlines AI Vision
Amazon CEO Outlines AI Vision
Amazon CEO reveals AI investment plans in new letter
 Osaka Hosts World Expo 2025
Osaka Hosts World Expo 2025
Japan blends tech and culture at Osaka Expo 2025 launch
 A16z Plans Big Bet on AI Startup
A16z Plans Big Bet on AI Startup
A16z may lead huge round in ex-OpenAI CTO’s new AI firm.
© MyEduGoal. All Rights Reserved. Design by markaziasolutions.com