


In today’s hyper-connected world, the old “castle and moat” model of cybersecurity — where everything inside a network is trusted — just doesn’t cut it anymore. Enter Zero Trust Architecture (ZTA), a modern, powerful approach to network security that says: “Never trust, always verify.”
Let’s unpack what this means, why it matters, and how students and educators can benefit from understanding it.
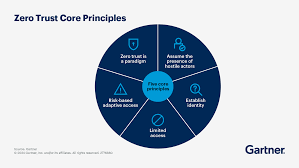
Zero Trust is a security model built around the idea that no one — not even people or devices inside your network — should be automatically trusted.
Whether you're a student logging in from a school Wi-Fi or a teacher accessing grades from home, every access request is verified, authenticated, and monitored.
✅ Key Principle: "Assume breach." Always operate as if an attacker is already inside the system.
In traditional security setups:
Once you’re inside the network (e.g., logged into your school system), you often have access to multiple systems.
Attackers who breach one point (like a weak password or stolen credentials) can move freely across the network.
With the rise of remote learning, cloud apps, and BYOD (Bring Your Own Device), this kind of open trust is a recipe for disaster.
Zero Trust doesn’t rely on a physical location (like being on-campus) to decide whether you’re safe. Instead, it considers:
Student, teacher, IT staff, outsider?
Is it a school-managed laptop or a personal phone?
Is it sensitive information like grades or public content?
School, home, café, another country?
Are they logging in at 2 AM from a new device? Red flag.
All of this information is checked every time someone tries to connect — no more “you’re inside, you’re trusted.”
| 🔐 Component | 📘 What It Means |
|---|---|
| Identity Verification | Confirming who you are (via login, biometrics, MFA) |
| Device Health Checks | Making sure your device is secure and up-to-date |
| Least Privilege Access | Giving users only the access they need, nothing more |
| Microsegmentation | Breaking the network into small, isolated zones to limit breach impact |
| Continuous Monitoring | Constantly watching for unusual behavior or signs of intrusion |
Protects against account takeovers, especially in cloud-based learning environments (like Google Classroom or Microsoft Teams).
Prevents ransomware from spreading across the whole school network.
Safeguards student records, grades, and financial information.
Supports secure remote learning, even from personal devices or public Wi-Fi.
Imagine a student logs into their online portal from a new device at midnight from a location they've never used. Under Zero Trust:
Their login would be flagged as unusual.
They might be asked for extra verification.
Access could be temporarily blocked until confirmed safe.
Requires strong identity management systems
May involve new tools and training
Needs ongoing monitoring and not just “set it and forget it”
But the payoff? Massively reduced risk, especially in environments with lots of users, devices, and cloud-based tools — like schools and universities.
| ✅ Old Model | ❌ Weakness |
|---|---|
| Trust insiders | Assumes everyone inside is safe |
| Wide access | Makes lateral attacks easy |
| Focused on perimeter | Doesn’t protect cloud or remote users |
| ✅ Zero Trust | ✅ Strength |
|---|---|
| Verify every user/device | Blocks unauthorized access early |
| Limited, need-based access | Reduces attack surface |
| Works with cloud/remote setups | Perfect for hybrid education |
As cyber threats evolve, Zero Trust Architecture is becoming the gold standard. Governments, corporations, and now schools are adopting this mindset to stay ahead of attacks. It’s not just an IT buzzword — it’s a crucial strategy for keeping students, educators, and their data safe.
#trending #latest

University Internships That Help You Get a Job After Graduation... Read More.

Is It Smarter to Start at a Community College... Read More.
 Fake posts hit Czech PM Fiala's X
Fake posts hit Czech PM Fiala's X
Fake posts disrupt Czech PM Fiala's X account security
 Switzerland Tightens Export Rules
Switzerland Tightens Export Rules
Switzerland expands export controls on dual-use goods
 Google unveils Ironwood AI chip
Google unveils Ironwood AI chip
Google introduces Ironwood chip to accelerate AI tasks & apps
 TSMC Q1 revenue up 42%
TSMC Q1 revenue up 42%
TSMC sees 42% revenue surge in Q1, surpassing forecasts
 Amazon CEO Outlines AI Vision
Amazon CEO Outlines AI Vision
Amazon CEO reveals AI investment plans in new letter
 Osaka Hosts World Expo 2025
Osaka Hosts World Expo 2025
Japan blends tech and culture at Osaka Expo 2025 launch
 A16z Plans Big Bet on AI Startup
A16z Plans Big Bet on AI Startup
A16z may lead huge round in ex-OpenAI CTO’s new AI firm.
© MyEduGoal. All Rights Reserved. Design by markaziasolutions.com