


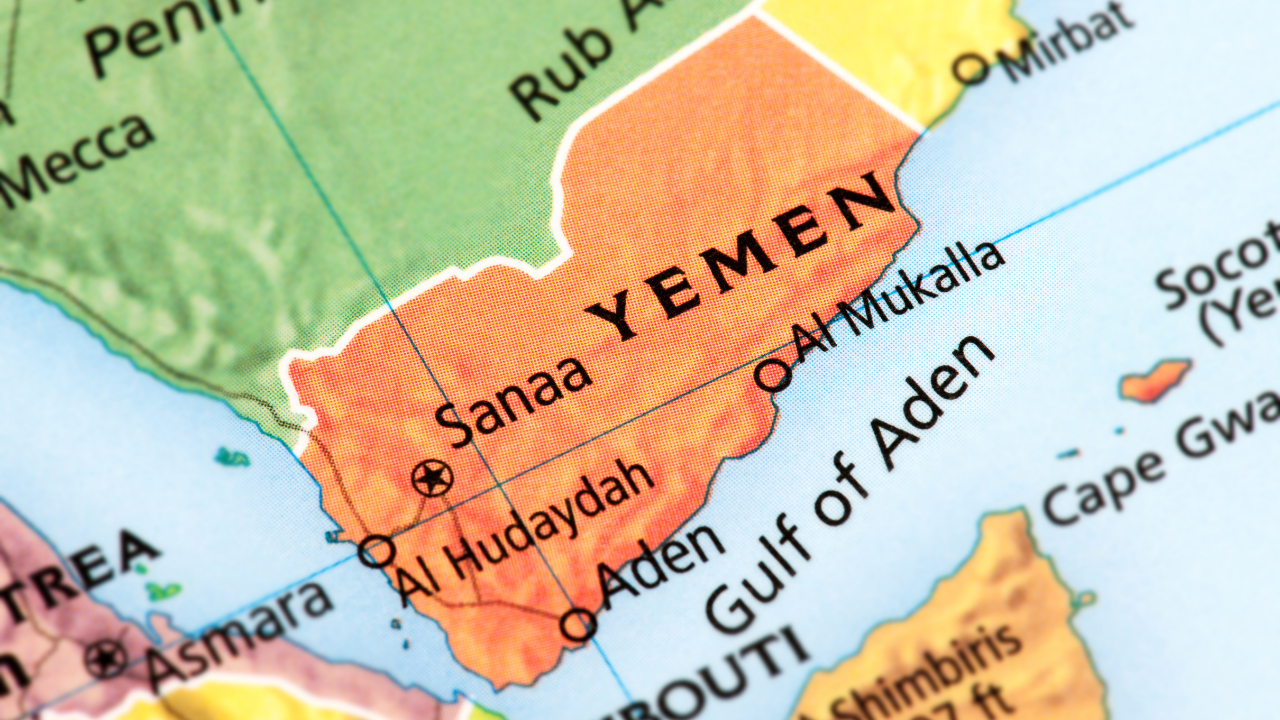
The leakage of Yemen strike plans via Signal, a supposedly secure messaging platform, is raising serious concerns among military and intelligence communities. While Signal is known for its end-to-end encryption, the sharing of classified military strategies—even on secure apps—can have devastating consequences.
The central issue lies in the nature of the content shared: military strike plans are highly sensitive and time-critical. Any unauthorized access or unintentional leak, even through a private Signal group, can compromise operational security, alert adversaries, and jeopardize lives. In the context of the Yemen conflict, where multiple regional and international actors are involved, the stakes are incredibly high.
Reports suggest that certain individuals with access to confidential information might have used Signal to discuss or distribute details of planned military operations targeting rebel-held areas in Yemen. This has led to concerns that hostile entities could have intercepted or been forwarded such messages, either accidentally or intentionally.
Even though Signal is designed with privacy in mind, human error and insider threats remain the biggest risks in secure communication systems. If the plans were shared without proper encryption settings or if screenshots were taken and leaked, the information could easily spread beyond the intended audience. This would provide opposition forces with time to fortify positions, flee targeted zones, or retaliate preemptively.
Furthermore, such a leak has the potential to damage international relations. Allies may begin to question the ability of involved forces to handle intelligence responsibly, leading to diplomatic friction or reevaluation of collaborative missions. The credibility of the forces responsible for the strike could be undermined both domestically and globally.
The incident also highlights a broader concern: the growing dependence on encrypted messaging apps in high-stakes environments without adequate protocols or safeguards. Military communication, ideally, should remain within secure and monitored systems that offer both privacy and control—unlike public apps.
In conclusion, the sharing of Yemen strike plans on Signal is a stark reminder that secure technology alone isn't enough. Strict adherence to protocol, proper training, and accountability are essential to maintaining operational integrity and protecting national interests. The incident serves as a wake-up call for governments and military forces worldwide to revisit their digital security policies and ensure such breaches do not recur.
#YemenCrisis #SignalLeak #MilitaryBreach #trending #latest #BreakingNews #MiddleEast #NationalSecurity

University Internships That Help You Get a Job After Graduation... Read More.

Is It Smarter to Start at a Community College... Read More.
 Fake posts hit Czech PM Fiala's X
Fake posts hit Czech PM Fiala's X
Fake posts disrupt Czech PM Fiala's X account security
 Switzerland Tightens Export Rules
Switzerland Tightens Export Rules
Switzerland expands export controls on dual-use goods
 Google unveils Ironwood AI chip
Google unveils Ironwood AI chip
Google introduces Ironwood chip to accelerate AI tasks & apps
 TSMC Q1 revenue up 42%
TSMC Q1 revenue up 42%
TSMC sees 42% revenue surge in Q1, surpassing forecasts
 Amazon CEO Outlines AI Vision
Amazon CEO Outlines AI Vision
Amazon CEO reveals AI investment plans in new letter
 Osaka Hosts World Expo 2025
Osaka Hosts World Expo 2025
Japan blends tech and culture at Osaka Expo 2025 launch
 A16z Plans Big Bet on AI Startup
A16z Plans Big Bet on AI Startup
A16z may lead huge round in ex-OpenAI CTO’s new AI firm.
© MyEduGoal. All Rights Reserved. Design by markaziasolutions.com